
There are many things that tie BlackBerry users together, and one of those has always been the importance of security. Some people forget that being secure means more than just ensuring an application is virus free! Nefarious (what a great word) applications can access private data, sneak that data out to private websites, and even monitor your device traffic to keep tabs on what your doing all without the user knowing. Real dangerous applications can go even farther, allowing a developer to remotely execute code on a users device without the users permission! Imagine, applications that can decide what you can and can’t do, search the internet for things without you knowing or perform actions on your phone without your knowledge.
Not only are these security concerns very real, but they go unnoticed by all major platforms during testing and validation cycles. No major device manufacturer at this time that I am aware of is monitoring applications submitted to their platforms for what data is being sent and received. Although, to give them credit, BlackBerry has done a fantastic job of limiting what applications with back-doors can do.
Read ahead to see how 12 applications perform back-to-back in a test for Web Security for BlackBerry 10 (Spoiler: They might not do as well as you think!).
Edit: Wow, less than an hour in and the assault has began! To everyone from Nemory Studios, attempts to harass and attack our contributors over social media will continue to be ignored. We wish you the best – however the easiest way to contact us has always been (and always will be) the giant Contact-Us link in the top corner! You can’t miss it – thanks! To readers, be cautious, as he has not reacted well to the transparency. Only share if you’re brave!
Edit #2: I’ve been asked about the actual logs. Tomorrow I will cleanup the fiddler logs (no private data for you hack types) and release the logs in the morning. The source code and decompiled binaries I can’t share obviously, you are on your own to get those. But I’ll do up a little article with it so that anyone can see what data is being sent just by using a simple proxy like Fiddler. I’ll also share some of the http strings being assembled by the Kelly class and why this one server poses a huge risk to users.
Edit #3: Logs, and some interesting information http://www.filearchivehaven.com/2015/02/09/follow-up-web-security-analysis-brief-how-to/
Purpose of the Article
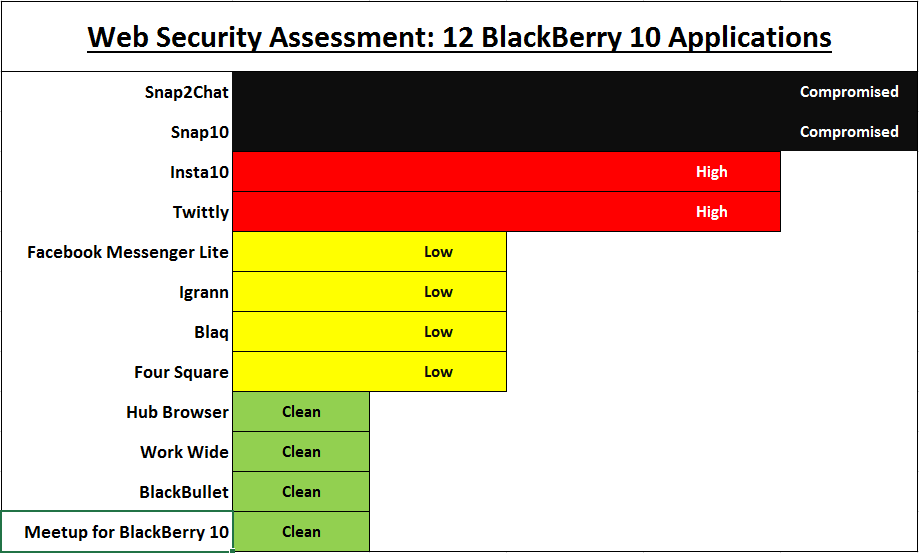
- Want the short version? Scroll down to see the graph (a bar graph is worth … well actually 2870 words).
The intent of this article is to share a high-level security analysis of 12 applications on BlackBerry 10 by monitoring their internet traffic and decompiling their BAR files when necessary. I’ve chosen applications focused on Social Media and upon recommendation from other developers. During the progression of testing, I have found applications from some certain developers to be higher risk than the others and I’ve broken them down as best I can below rated from most-tricky to least-risky (see what I did there).
A Note on Data Collection
There are plenty of valid reasons why a developer may be collecting data. They may want to know how many keyboard phones are having a particular crash issue, or they need to prove their users really exist to advertisement companies. What defines legitimate data use is a much more complicated topic and changes from country to country. I’ve done my best to break apart the legitimate collection (and proper handling) of data from the suspicious as I moved through the applications.
At the end of the day its up to the developer to share their privacy policy with you and to ensure they disclose what they use the information for. If they collect or give away data that identifies you as an individual, you must be aware of it and you must agree to it. Users should never be afraid to ask a developer what they are collecting and what they are using the information for, but at the same time, its always best to assume they are collecting data for a legitimate reason when reaching out to them for the first time.
Download Links Ranked by Risk:
- Snap2Chat (no longer available) Risk: Compromised
- Snap10 Risk: Compromised
- Insta10 (only available through Beta Zone) Risk: High
- Twittly Risk: High
- Facebook Messenger Lite Risk: Low
- Igrann Risk: Low
- Blaq Risk: Low
- Four Square Risk: Low
- Hub Browser Risk: Clean
- Work Wide Risk: Clean
- BlackPullet Risk: Clean
- Meetup for BlackBerry 10 Risk: Clean
Application Breakdown (Ranked by Risk)
Snap2Chat by Nemory Studios
Status: Compromised
Summary: This application is an extremely high risk application with potential remote execution scripts embedded per the developers statements online. In testing, it connected to Snapchat 2x for every ~340x internet connections it made meaning it has the potential to use up-to 300 times the bandwidth compared to the official Snapchat application. It connected to a dozen websites in addition to the Snapchat website, and requested a total of 10 permissions. The application submitted hundreds of hidden advertisement requests to Smaato but did not show them to the user. More importantly, it is submitting user data including name, gender, age etc. in plain text over the internet to a hidden Nemory Studios website.
Permissions requested: Camera, BBM (Invite + Profile Access), Shared Files, User PIN + Device Info, Location, Microphone, Screen Capture, Background Processing & Contacts
Addendum: Nemory has advised the data he is submitting is limited to only the User ID. I can validate that no passwords appear to be sent, however, the amount of data attempting to submit to his server appears to be version specific. Additional testing may be required.
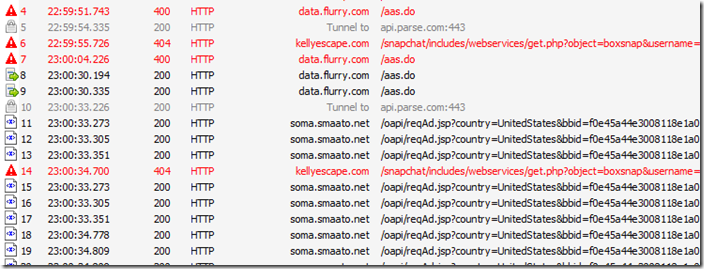
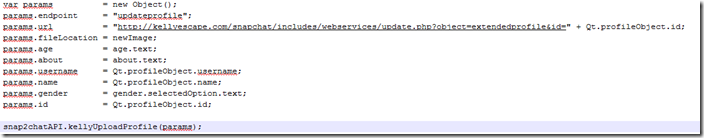
Data sharing: I saw analytics being submitted to http://data.flurry.com (potentially by BlackBerry themselves) on launch, close, minimize and full-screen of the application. The app then sends user data through http://api.parse.com also for analytics. It sends and stores information a third time to Google analytics this time. And finally it then submits private user data in plain text over regular HTTP to a website called http://kellyescape.com. The application queries Kelly Escape many times and plain text data means your personal information is fully viewable by anyone else on the same network as you and anyone between KellyEscape.com and you. Checking the BAR file itself we can see it has dozens of hooks into this hidden website and submits everything from your extended profile to your login information. The main developer for this application has loosely admitted to using Remote Execution scripts in the past (although he also later denied both collecting user information and running remote execution scripts) and has also alluded to targeting users using data collection. This application is pulling advertisement and news information from www.blogblog.com, which opens the advert and application display information to a risk of hijacking (see below in conclusion about the risks of third party sites for data storage). It then contacts another server http://nemorystudios.blogspot.ca when queried about registration methods (spoiler: There are none, its an click-bait) further increasing the likelihood of the URL and advertisement mediums being hijacked. It finally is also pulling advertisements from http://smaato.net without displaying them to the actual users and playing them in the background.
Additional notes: Snapchat has filed a cease and desist against the developer for charging for the service and using their name and logo. Snapchat has been warning they will shut-down user accounts accessing their site through this app and Snap2Chat itself is no longer available in BlackBerry World. The developer has informed users that this is the risk they take with the application. And regardless of the misleading communication on the developers website you actually just need to fill out a form at BlackBerry for a refund – the same as with any BlackBerry 10 application.
Terms of Service: This application is not authorized by Snapchat and violates terms of service on BlackBerry, Smaato, and Snapchat. As well as privacy laws in several countries for data collection without notifying users (putting user accounts at risk through use of the application).
- Unencrypted connections: http://data.flurry.com, http://api.parse.com, http://files.parsetfss.com, http://blogblog.com, http://nemorystudios.blogspot.ca, http://ih6.googleusercontent.com, http://smaato.net , http://www.kellyescape.com
- Encrypted connections: https://www.snapchat.com
Snap10 by Nemory Studios
Status: Compromised
Summary: This application is an identical risk to Snap2Chat. Whew easy one.
Facebook Chat by Nemory Studios
Status: Low Risk
Summary: It appears the data it is trying to send and receive from http://www.kellyescape.com is a URL the developer can enable and disable at will. The application uses about 10x the traffic required to connect to Facebook by interfacing with analytics, submitting user data of some kind for analytics through KellyEscape.com again. However, because the data it gathered and submitted was of low value, I have marked it as a low risk.
Permissions requested: BBM (Invite + Profile Access), Shared Files, User PIN + Device Info, Location, Microphone. And then requests extra permissions through Facebook for the users personal profile, ability to submit messages on behalf of the user, and friends chat status.
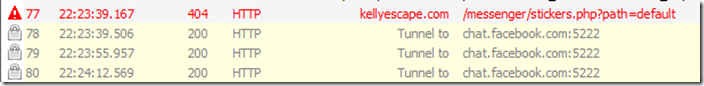
Data sharing: Analytics (potentially by BlackBerry) is submitted to http://data.flurry.com on launch, close, minimize and full-screen. It also pulls some files and data through http://www.kellyescape.com and gathers additional files from http://www.facebook.com (unencrypted). It then started sending data out to Google analytics. For the most part it appears to be using https://m.facebook.com and https://chat.facebook.com on port 5222 and https://edge-chat.facebook.com. It sends data to http://cloudfront.net, and eventually stated trying to send data again out to http://www.kellyescape.com/messenger. I am unsure what it is doing with Cloud Front.
Terms of Service: This application does not appear to be authorized by Facebook, which places it in violation of both Facebook and BlackBerry terms of service (putting user accounts at risk through use of the application).
- Unencrypted connections: http://data.flurry.com, http://www.kellyescape.com, http://cloudfront.net
- Encrypted connections: https://www.facebook.com
IGrann by Adrian Sacchi
Status: Low Risk
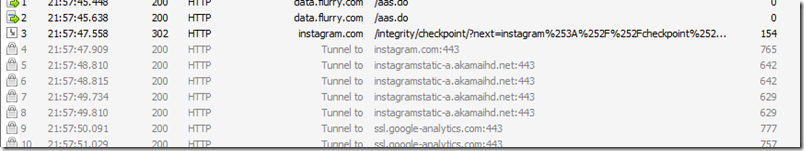
Summary: The application submitted all its data to Instragram over secured connections with the exception analytics call outs to Google Analytics. It retrieved some photos over unsecured, however, they are public photos with access to all users – and it appears to be a design by Instragram.
Permissions requested: No permissions were requested.
Data sharing: Analytics (potentially by BlackBerry) were submitted to http://data.flurry.com on launch, close, minimize and full-screen. Next the application started to send data to Google Analytics. Otherwise connecting only to Instagram.
Terms of Service: This application performed the correct handshake with Instagram API’s, and leveraged official Instragram API URLs. Correction: I’ve been advised the API is only approved for read-only access, therefore, use at your own discretion!
- Unencrypted connections: http://instagram.com, http://data.flurry.com
- Encrypted connections: https://instagram.com, http://ssl.google-analytics.com
Insta10 by Nemory Studios
Status: High-Risk
Summary: Due to the unknown nature of the access to the Amazon AWS cloud server found while using Insta10, the series of hidden Smaato requests it made and the fact it bypassed important hooks for official Instagram API support, it is likely accounts could be banned using this application to connect to Instagram (which is also mentioned by users in the reviews as becoming an issue). Additionally, because web services have been created on KellyEscape.com, this is raised to a high-risk as it is likely it will follow the same framework as Snap10 for collecting personal data over unencrypted data channels.
Permissions requested: BBM (Invite + Profile Access), Shared Files, User PIN + Device Info, Location, Microphone, Screen Capture, Notifications, Contacts.
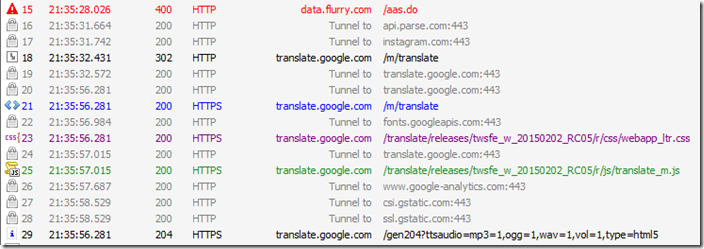
Data sharing: Analytics (potentially by BlackBerry) were submitted to http://data.flurry.com on launch, close, minimize and full-screen. It sent encrypted data to http://translate.google.com and collected and downloaded JS files, CSS files and HTML files for local use (reason unknown – but this presents a security risk as JavaScript files downloaded this way would have the same access to your BlackBerry as the application itself – a major risk of hijacking your phone). It then sent data to Google Analytics using http://www.gstatic.com. It did not appear to access official API’s or to send the API handshake expected for approved API connections to Instragram. During more involved use, it connects to an Amazon AWS cloud server (data submitted or reason unknown) and tumblr for news data. Finally it submitted a series of hidden advertisement requests to Smaato. The advertisements it discovered were not shown to the user, and recycled in the background.
Moving one level deeper, we can see integration has been added to http://www.kellyescape.com to support Instragram hooks likely to come via an update, but they do not appear to be in the betazone version of the application.
Terms of Service: This application does not use standard approved API connections for Instragram. It appears to break the Smaato terms of service. It is likely to start using KellyEscape.com to store user private data, and currently breaks BlackBerry terms of service regarding third party API.
- Unencrypted connections: http://data.flurry.com, http://www.kellyescape.com, http://www.gstatic.com, http://translate.google.com, http://parsetfss.com
- Encrypted connections: https://www.instagram.com
Blaq by Kisai Labs
Status: Low-Risk
Summary: There was some activity to a local port but otherwise just used Twitter.
Permissions requested: BBM (Invite + Profile Access), Shared Files, User PIN + Device Info, Background Application
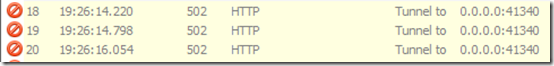
Data sharing: Analytics (potentially by BlackBerry) was submitted to http://data.flurry.com on launch, close, minimize and full-screen. The only other URL of mention within the app was information sent from their home server at http://blaq.kisailabs.com and profile pictures from the owners via Instagram while retrieving the About page. Otherwise, all connections were made to http://abs.twing.com over encrypted channels, and http://api.twitter.com again over encrypted channels. It did seem to be trying to connect to an unusual port (0.0.0.0:41340) during use, but I’ve kept this a Low Risk as the IP 0.0.0.0 will not resolve on a device.
Terms of Service: This application appears to follow Twitter API rules and conventions.
- Unencrypted connections: http://data.flurry.com, http://blaq.kisailabs.com
- Encrypted connections: https://www.twitter.com, http://abs.twing.com
Twittly by Nemory Studios
Status: High-Risk
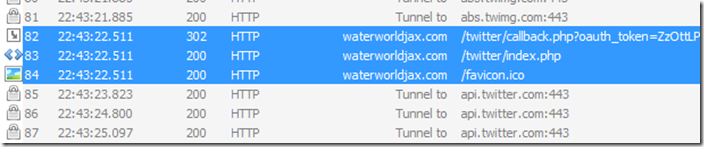
Summary: For the most part the application is submitting analytics and downloading unusual data from Google translate. It is also looping links through either a hacked website, or someone else’s website, using PHP files stored on http://waterworldjax.com – this is a major security risk from hijacking. Because all the data is submitted over HTTP in plain text, it is high risk for someone to steal the information. The bounce URL is suspicious enough to move this from medium to high risk.
Permissions requested: BBM (Invite + Profile Access), Shared Files, User PIN + Device Info, Location, Microphone. And then requests extra permissions through Facebook for the users personal profile, ability to submit messages on behalf of the user, and friends chat status.
Data sharing: Analytics (potentially by BlackBerry) were submitted to http://data.flurry.com on launch, close, minimize and full-screen. It is running data through http://translate.google.com again, and back through Google Analytics. It also pulls some data from http://waterworldjax.com/twitter/redirect.php which is a highly unusual location for a redirect auth-request for an application, and analytics aside, mostly stayed within the Twitter API boundaries. At one point, it started sending large amounts of data to Smaato again and requested approximately 10 advertisements per-second with no advertisements viewable to the user.
Terms of Service: This application appears to follow Twitter API rules and conventions however it also appears to be breaking Smaato terms of service.
- Unencrypted connections: http://data.flurry.com, http://www.waterworldjax.com
- Encrypted connections: https://www.twitter.com
FourSquare by foursquare
Status: Low-Risk
Summary: Nothing to report.
Permissions requested: Unknown
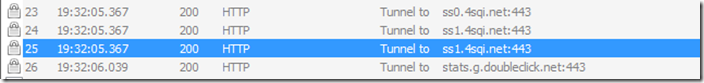
Data sharing: Analytics (potentially by BlackBerry) is submitted to http://data.flurry.com on launch, close, minimize and full-screen. The only other data is encrypted data sent to http://api.foursquare.com and http://ss1.4sqi.net. Later I did see a reference to an analytics engine http://www.doubleclick.net.
Terms of Service: This application appears to as official as you can get.
- Unencrypted connections: http://data.flurry.com
- Encrypted connections: http://api.foursquare.com, http://ss0.4sqi.net, http://ss1.4sqi.net
Hub Browser by Tundra Core Studios
Status: Clean
Summary: Nothing to report.
Permissions requested: None.
Data sharing: On launch, the application did not access the internet. When directed to access a website, only the website was accessed.
Terms of Service: This application breaks no terms of service.
- Unencrypted connections: None
- Encrypted connections: None
Work Wide by Brian Scheirer
Status: Clean
Summary: Nothing to report.
Permissions requested: None.
Data sharing: On launch, the application did not access the internet. When directed to access a website, only the website was accessed.
Terms of Service: This application breaks no terms of service.
- Unencrypted connections: None
- Encrypted connections: None
BlackBullet by QtHelex
Status: Clean
Summary: Nothing to report.
Permissions requested: None.
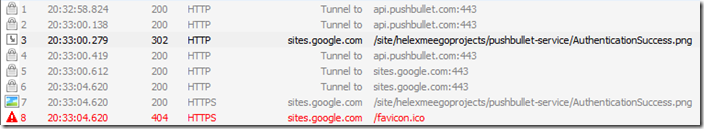
Data sharing: On launch, the application only accessed Push Bullets servers using the official API link. It downloaded images from a Google site, https://sites.google.com/site/helexmeegoprojects/ which appears to be the home site of the creator.
Terms of Service: This application appears to break no terms of service.
- Unencrypted connections: http://sites.google.com
- Encrypted connections: http://api.pushbullet.com
Meetup for BlackBerry 10 by Dean Logic
Status: Clean
Summary: Nothing to report.
Permissions requested: None.
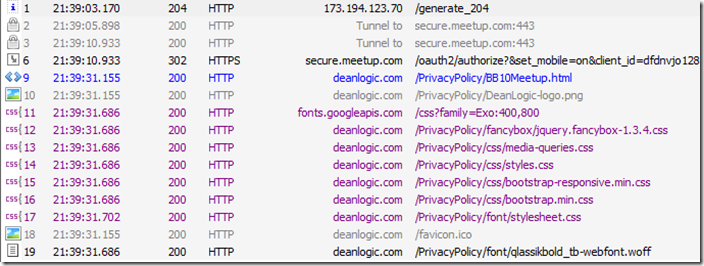
Data sharing: The application is clean, it checked only https://secure.meetup.com for data, made an appropriate handshake, and pulled the privacy policy from the creators home site.
Terms of Service: This application appears to break no terms of service. The developer has validated the application with the Meetup team.
- Unencrypted connections: http://www.deanlogic.com
- Encrypted connections: https://secure.meetup.com
Conclusion
This is far from the most robust way to analyze and test applications, but as you can see, these applications have a vast difference in footprint from one to another in terms of security, risk and internet usage.
When looking for secure applications keep these tips in mind:
- Be cautious of applications that don’t connect directly to a the service you expect. If it goes through a third-party website, that website can be hijacked to get access to you! And if the application is sending data to 12 different websites, that’s 12 different opportunities for someone to get access to your information that the developer has reduced control over.
- Don’t be afraid to ask tough questions. Your data is yours, you should not have to hand it over without someone telling you what they are collecting, why they are collecting it and who they are sending it to.
- Call out people who break policies and terms of service. Someone who creates a pretend social media application without authorization isn’t really from from that company. They don’t build the API’s or Servers and they don’t decide the rules. They are charging you for a service they don’t own, aren’t actually supporting and in many cases, don’t even understand. And if things go sideways – they won’t be standing next to you fighting to get your accounts or passwords back.
- Don’t trust applications from developers where support is incomplete or contradicts BlackBerry support sites. Be very cautious of people who use emotional, unprofessional or slang terminology with their clients.
That’s it for the long article on some applications – but don’t let it stop here! You can use applications like Fiddler as a proxy to check what an application is doing. Or if you know how, you can disassemble applications yourself and see what URL’s they are being told to connect to. Most of all, don’t be afraid to do your own independent research and to ask hard questions when you need to.
Do you think there are any good applications that were missed? If you have an application you’d like me to review, or know a free one you’d like me to test out then just drop a line in the comments!
Thank you very much for the quick reply, your thoughts and of course, the app redemption code. Did it. And, will start using it. cameron
No problem! If the notifications drive you nuts, you can disable them all under Headless in Settings 🙂
When you say «and decompiling their BAR files when necessary», which methods did you use? Could you be a little more technical about it? Bests.